HTTP強制安全傳輸技術(HTTP Strict Transport Security, HSTS)是一個網際網路的安全策略機制,讓網頁伺服器設定一個時間,限制用戶端的瀏覽器在該時間內,只能夠使用安全的HTTPS連線方式(HTTP強制轉成HTTPS連線),瀏覽該網站內容,以減少連線被劫持的風險。HSTS也算是一套很成熟的安全性增強的應用了,只需要有SSL認證即可,我近幾年都是用VestaCP,所以這邊做個開啟HSTS的紀錄方便查閱 🤖
NGiNX設定
|
1 2 3 4 5 |
rm -f /etc/nginx/conf.d/default.conf.bak cp /etc/nginx/conf.d/default.conf /etc/nginx/conf.d/default.conf.bak sed -i '/server_name/a add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;' /etc/nginx/conf.d/default.conf sed -i '/server_name/a add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;' /home/admin/conf/web/*.nginx.ssl.conf sed -i 's/443 ssl/443 http2 ssl/g' /home/admin/conf/web/*.nginx.ssl.conf |
Apache設定
↓↓↓↓↓此為非必要選項↓↓↓↓↓
|
1 2 3 4 5 6 7 8 9 10 11 12 |
rm -f /etc/httpd/conf/httpd.conf.bak cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.bak cat >> /etc/httpd/conf/httpd.conf <<- EOF ########## Setting up HSTS ########### # Enable Headers and rewrite modules LoadModule headers_module /usr/lib64/httpd/modules/mod_headers.so LoadModule rewrite_module /usr/lib64/httpd/modules/mod_rewrite.so # Setting up: https://is.gd/BqzkAj # ref. https://hstspreload.org Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload" ########## Setting up HSTS ########### EOF |
↑↑↑↑↑ 此為非必要選項 ↑↑↑↑↑
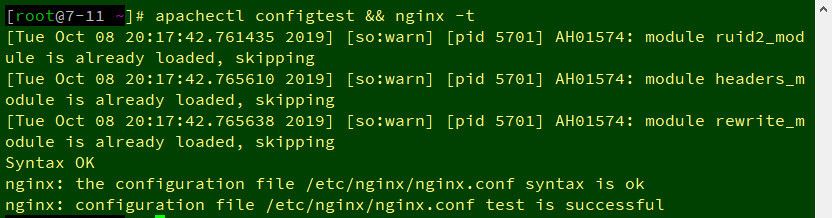
###最終測試
|
1 |
apachectl configtest && nginx -t |
只要有出現下列三行即可 🤖
|
1 2 3 |
Syntax OK nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful |
###重啟網頁前端
systemctl restart httpd && systemctl restart nginx
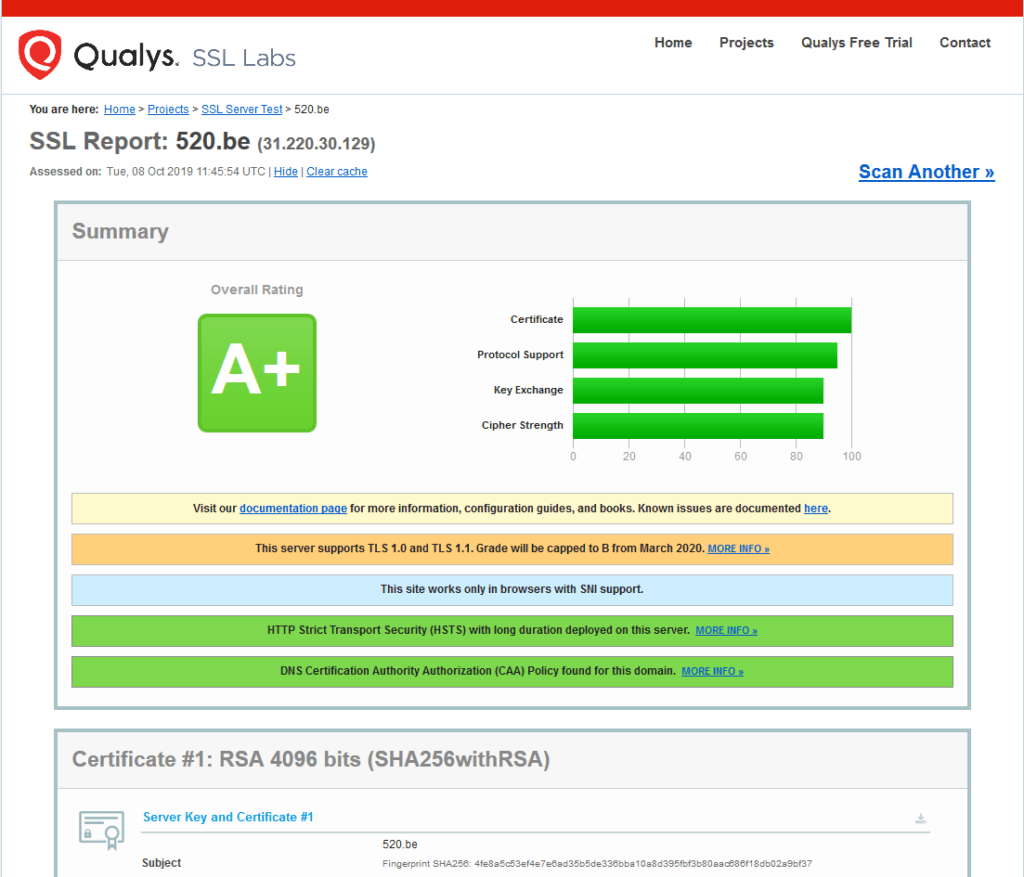
然後到Qualys. SSL labs檢測,我的已經是A+等級了 🤖
ref.
- IBM HTTP Server – 設定 HTTP 嚴格傳輸安全 (HSTS)
- HTTP Strict Transport Security (HSTS) and NGINX
- MDN Web Docs – Strict-Transport-Security
- Google擴大HSTS應用範圍,確保旗下更多網站安全性
 列印本文
列印本文
 逆向行駛 最愛的最殘酷、最美的最虛無
逆向行駛 最愛的最殘酷、最美的最虛無
![[animagine-xl-3.1] Hawaii, USA - 013](https://520.be/wp-content/uploads/2019/10/animagine-xl-3.1-Hawaii-USA-013-660x330.jpg)