Google、Cisco、Akamai、Mozilla、IdenTrust、蘋果、微軟等等的公司合推的非營利、開源、免費SSL認證的網路認證發放機構Let’s Encrypt從去年秋季開始發放免費但限期3個月SSL簽證(可無限續期)之後,陸續已經超過有3百多萬個網站使用,我也順便這兩天玩了一下,簡單做個記錄。 ?
1.安裝Bc、git、EPEL來源
yum -y install git bc epel-release
2-1.git方式下載Let’s Encrypt(推薦)
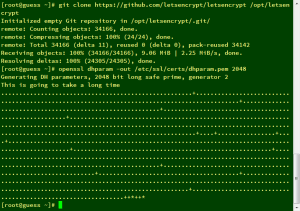
git clone https://github.com/letsencrypt/letsencrypt /opt/letsencrypt
2-2.一般方式下載Let’s Encrypt
|
1 2 3 4 5 |
cd /opt/ wget https://github.com/letsencrypt/letsencrypt/archive/v0.5.0.tar.gz tar xf v*.tar.gz -C /opt/ mv letsencrypt-* letsencrypt cd /opt/letsencrypt |
3.以Diffie-Hellman(迪菲-赫爾曼)交換演算法產生密鑰
openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048
4.申請Let’s Encrypt認證,請注意修改以下三項:
admin@guess.za.net = 修改成使用中的信箱
guess.za.net = 修改成要申請的域名
/home/wwwroot/default/ = 修改成主機的網頁根目錄
mkdir -p /home/wwwroot/guess.za.net/.well-known/acme-challenge
cd /opt/letsencrypt
./letsencrypt-auto certonly --email admin@guess.za.net -d "guess.za.net" --webroot -w /home/wwwroot/guess.za.net/ --agree-tos
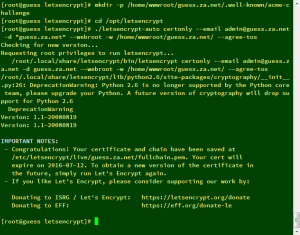
成功後會產生三個檔案,位置分別是:
/etc/ssl/certs/dhparam.pem
/etc/letsencrypt/live/guess.za.net/fullchain.pem
/etc/letsencrypt/live/guess.za.net/privkey.pem
5.設定NGiNX檔案,在server區段內新增
※請注意修改成實際產生的位置※
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
listen 443 ssl; ssl_dhparam /etc/ssl/certs/dhparam.pem; ssl_certificate /etc/letsencrypt/live/guess.za.net/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/guess.za.net/privkey.pem; ssl on; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA'; ssl_session_timeout 1d; ssl_session_cache shared:SSL:50m; ssl_stapling on; ssl_stapling_verify on; add_header Strict-Transport-Security "max-age=31536000; includeSubDomains"; |
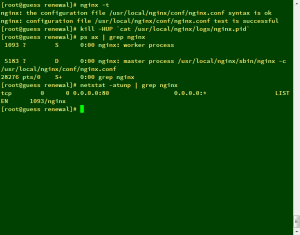
設定完畢後先用此指令測試設定檔有無出錯
nginx -t
確認沒問題之後才重啟NGiNX,然後前往ssllabs.com檢查SSL認證狀態
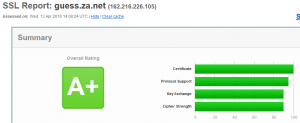
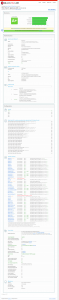
nginx -s reload
ps ax | grep nginx
netstat -atunp | grep nginx
6.新增Let’s Encrypt的設定檔來自動更新SSL
※請注意修改成使用中的信箱、要申請的域名、主機的網頁根目錄※
|
1 2 3 |
mkdir -p /var/log/letsencrypt/ mkdir -p /etc/letsencrypt/configs cat >> /etc/letsencrypt/configs/guess.za.net.conf < |
7.新增自動更新SSL認證的SH檔案,內容如下:
※請注意修改成實際設定檔的位置※
vi /root/renew-letsencrypt.sh
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
#!/bin/sh cd /opt/letsencrypt/ ./letsencrypt-auto certonly --config /etc/letsencrypt/configs/111.net.conf --agree-tos --renew-by-default ./letsencrypt-auto certonly --config /etc/letsencrypt/configs/222.net.conf --agree-tos --renew-by-default ./letsencrypt-auto certonly --config /etc/letsencrypt/configs/333.net.conf --agree-tos --renew-by-default if [ $? -ne 0 ] then ERRORLOG=`tail /var/log/letsencrypt/letsencrypt.log` echo -e "The Let's Encrypt cert has not been renewed! \n \n" \ $ERRORLOG else nginx -s reload fi exit 0 |
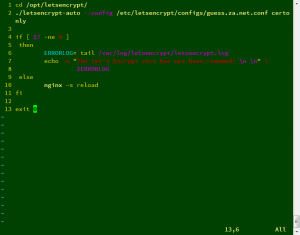
記得給權限唷 ?
chmod +x /root/renew-letsencrypt.sh
8.設定自動排程,每月1號自動更新SSL認證
crontab -e
@monthly cd /opt/letsencrypt && git pull
@monthly /root/renew-letsencrypt.sh
http://letsencrypt.readthedocs.org/en/latest/using.html
https://www.godaddy.com/help/install-a-lets-encrypt-ssl-nginx-20246
https://codex.wordpress.org/Nginx
https://www.nginx.com/blog/free-certificates-lets-encrypt-and-nginx/
https://www.digitalocean.com/community/tutorials/how-to-secure-nginx-with-let-s-encrypt-on-centos-7
 列印本文
列印本文
 逆向行駛 最愛的最殘酷、最美的最虛無
逆向行駛 最愛的最殘酷、最美的最虛無